What is Solar Winds Hack?
SolarWinds is an IT agency that gives software program for entities
Including Fortune 500 companies.
It was initially reported that SolarWinds was the topic of a large
cybersecurity assault that passed on to the company's clients.
The breach went undetected for months of impacted clients which included
TOP US Govt Agencies including the white house.
Earlier this year, hackers secretly broke into Solar Winds Programs and
added malicious code into the company's software. The system, often called
"Orion" is also used by corporations to take care of IT
Infrastructure and networks. Solarwinds has round 33,000 purchasers that use
Orion.
• Most software providers
regularly send out updates to their systems, whether it's fixing a bug or
adding new features. SolarWinds is no exception. Beginning as early as March
2020, SolarWinds unknowingly sent out software updates to its customers that
included the hacked code. The Hacked is commonly called as "SUNBURST"
Malware.
The code created a backdoor to customer's information technology systems,
which hackers then used to install even more malware that helped them spy on
companies and organizations.
• The hack went undetected
for months and was in stealth mode before being detected by any of the known
detection and control put in place by
organization's .This could accelerate
broad changes in the cybersecurity industry. Companies are turning to a new
method of assuming that there are already breaches, rather than merely reacting
to attacks after they are found.
Mitigation steps and
Recommendations
If you do not have solar winds Orion Systems/Network management software in your network ,you need not worry .But
would advise running a software inventory check of your network for possible Trial versions or evaluation
versions of Solar winds Orion or other products installed by your
systems/network administrators without your knowledge.
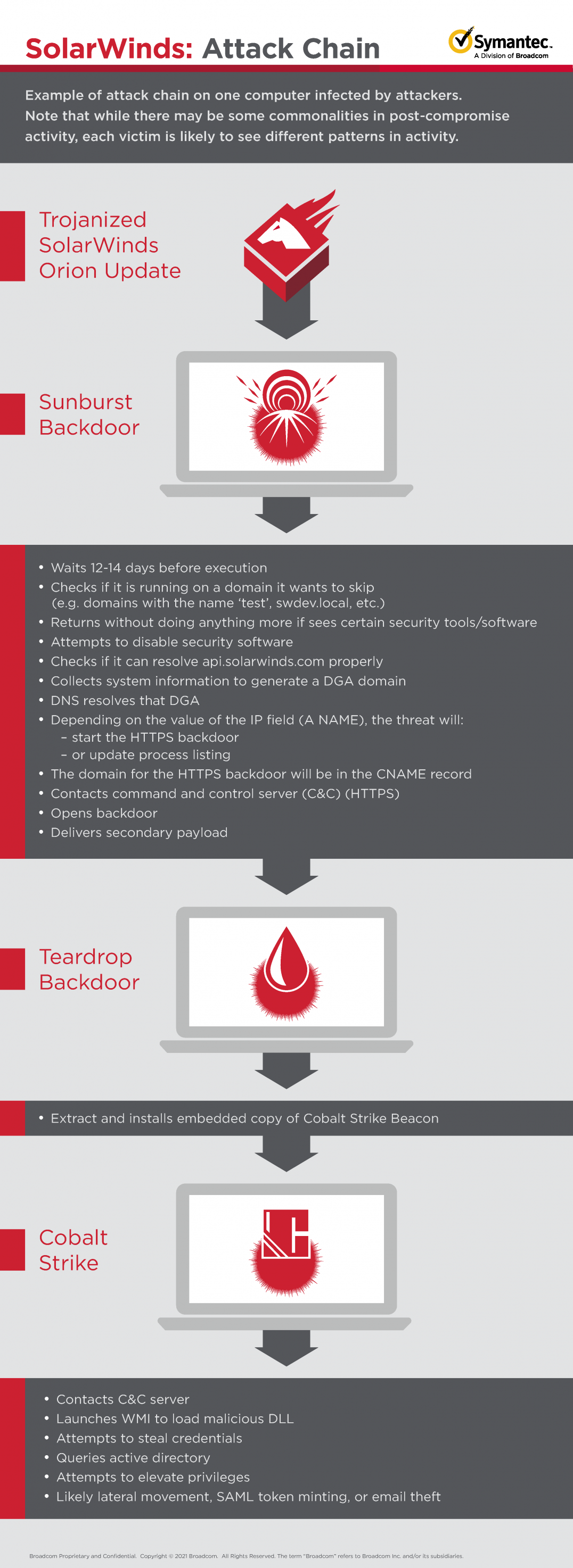
A simplified image of Solar Windows Attack as per Symantec is shown below
As you can see from the above illustration from Symantec(Broadcom) , The Sunburst Malware has the
ability to steal credentials including that of your systems administrator
Recommended Actions by Symantec(Broadcom)
Orion users should update to Orion Platform version 2020.2.1 HF 2.
Orion users should check their networks for indications
of post-compromise activity, including:
Use of Teardrop in-memory malware to
drop Cobalt Strike Beacon.
Command and control (C&C)
infrastructure leaks the configured hostname in RDP SSL certificates. Scanning
for your organization’s hostnames can uncover malicious IP addresses used by
the attackers, indicating post-compromise activity.
Geolocation of IP addresses used for
remote access may reveal if a compromised account is being simultaneously used
by a legitimate user and the attackers.
The attackers use multiple IP addresses
per VPS provider. If a malicious login from an unusual ASN(Autonomous System
Number) is identified, other logins from that ASN may also be malicious.
Logs for SMB sessions may show access to
legitimate directories and follow a delete-create-execute-delete-create pattern
in a short period of time.
It should be kept in mind that although there may be some
commonalities in post-compromise activity, each victim is likely to see
different patterns in activity. That activity is likely to involve heavy use of
living-off-the-land techniques to minimize the likelihood of being detected,
something the attackers seem to be prioritizing based on how they conducted the
first stages of the attack.
ShivaPrasad Ariga
No comments:
Post a Comment